In my experience, “If it isn’t broken, why fix it?” is the common train of thought that is shared between business owners in regards to their technology. I understand that decision-makers typically have countless other resources to manage and cannot be reasonably expected to stay up-to-date on the changing landscape of modern business technology. While larger corporations may have an IT department to handle this, most small businesses simply do not have those resources. Having managed IT projects for companies in many different verticals I’m hoping it will benefit others if I take a moment to discuss the common pitfalls and mistakes that are made in regards to the technology used by small businesses. I see these mistakes more often than I believe I should, and my goal is to not only describe what to do, but to also explain how and why these issues may affect your business.
What many small businesses tend to not realize is that their technology may be one of the largest investments that they make and it deserves to be proactively maintained. It’s not only the massive failures that we need to consider (such as natural disasters), but also the time we lose dealing with inefficient software, slowdowns, and security issues. Over time, the cost of dealing with relatively minor issues can add up to a significant amount of lost hours and revenue.
What many of the points in the following list will share in common is that they involve preventative care and proactive maintenance. For each point, take a moment to assess the cost of proactive maintenance over the potential costs of downtime, emergency service, and lost revenue. Often, the overall costs of fixing an unplanned failure are much more than the costs of proactive care. For the same reason our dentists ask us to brush our teeth to prevent cavities, keeping technology up-to-date can prevent expensive and time-consuming issues down the road.
Mistake #1: Failure To Perform Regular Data Backups
Ask yourself this: What would happen to your business if a natural disaster destroyed your office today? What if a hard drive with critical data failed? How quickly could your business be back up and running?

I placed backups first on the list because they are a necessary insurance policy to protect your business. I am still amazed by the amount of companies that I visit who are in emergency mode because they had no backup plan in place after experiencing a critical failure. No work can be performed and many hours are spent attempting to salvage the incident. Revenue is lost, and additional costs are spent on emergency repairs. Malware hijacking, failed hardware, and even an accidentally deleted file by an employee are all examples of situations where having a backup in place can save an incredible amount of time and heartache.
The need to establish a reliable backup strategy is especially important if you run a small business because emergency data recovery will be a painful and expensive process. The best way to manage data loss is to prepare for it before it occurs, and companies should be applying business continuity and data protection measures throughout their entire data lifecycle if one is not already in place.
Some backup solutions can have your business up and running in a matter of few hours, and there are many options to choose from to fit your needs. Some can be automated and require little to no work by an employee to manage. With the recent emergence of the “cloud,” company data can be stored virtually on a server as opposed to being stored locally on hard drives. This means that even if a natural disaster destroyed your business, your data can still be retrieved and restored.
Mistake #2: Over-Extending The Life Of Technology
Outdated technology is one of the more common mistakes businesses make that can lead to a plethora of other issues. Examples of technology that becomes outdated are operating systems, hardware, and software. Try to avoid taking the “cheap” route and sourcing older hardware and software, because the length of life of that technology may be shortened which increases the likelihood of running into conflicts and failures.

The Windows XP operating system is a great example. There are small businesses who are still running Windows XP on their work machines, and that operating system is no longer supported by Microsoft as of 2014. The computer may seem to function normally and warrant no replacement, but what users may not be aware of are the critical risks associated with running an operating system that is no longer being updated. For example, if a malicious hacker discovers an exploit that works with Windows, Microsoft will release an update to resolve the security issue across all of the operating systems they support. In this case, Microsoft would not include Windows XP among the updates. Knowing this, hackers may be biased towards targeting Windows XP machines with the knowledge that their exploit will be successful. If you’re still running Windows XP then the point has already been reached that your machines are potentially vulnerable to data hijacking and theft much more so than a more recent operating system.
Additional items to keep in mind are hardware such as hard drives. Hard drives have an average life span of approximately three to five years. This is not absolute, however, as many variables affect a hard drive’s life span and its performance. Some hard drives may defy age and last much longer, while others may die quickly for unknown reasons. A noisy or slow-performing workstation may be showing signs of failing hardware. Take a moment to assess the costs of an upgrade or replacement for one hard drive over the potential costs of a failure in terms of downtime, cost to repair, and lost revenue. What would happen if an important hard drive failed at your company? Do you have a backup solution in place?
Mistake #3: Poor Antivirus and Malware Protection
At a minimum small businesses will need anti-virus software, malware protection, and a strong firewall. Malicious individuals know that smaller companies make easier targets because many small businesses do not invest the time and money to implement solid security. It’s irresponsible to leave your business exposed to hackers and potentially devastating malware because it only takes one infection to halt workflow, damage your reputation, and lose important data.
“Cryptolocker,” a particularly malicious form of malware known as ransomware, is reported to have extorted as much as $ 3 million from users and businesses over an 8-month period from September 2013 to May 2014. It accomplished this feat by infecting every single file that the initial PC had access to (including anything on the network) and encrypted the files so that they were locked and inaccessible without a paid key, which only the hackers had and would not release without payment. The only way to unlock and retrieve files was to pay the creators of the malware a certain sum of money. In other words, it only took opening one file by a careless employee to completely shutdown business operations. The investment in security software and employee training will be small compared to the amount lost while trying to resolve such infections.
If you’re running a small business and currently have no antivirus software, I’d suggest looking into a solution as soon as possible. In the meantime, I’d suggest installing MalwareBytes as an option for malware removal that may help in the case of a minor infection (such as adware). The free version of MalwareBytes is not a single solution and does not monitor your workstations and server. However, it is reputable, free, and it may help you remove an infection from a workstation if one occurs.
Mistake #4: Irresponsible Passwords
It’s best practice to give each user their own profile and password for doing work. Do not allow the same password to be used across different devices. For example, don’t allow the password to access the wifi to be the same one used to access a server where critical information is stored. I use this example because there have been occasions where a wifi password was provided to a visiting friend or client at a company, and that individual took it upon themselves to snoop around and access other critical information using the same password.
There is always the risk that a device may fall into the wrong hands. For example, an employee may lose a work laptop or phone, and the curious individual who finds it may try to access it. Chances are they may try a variety of simple passwords to access the device, such as “password” or “123456.” If this does not work, they could try using special software to expose what the password to access the device is (and yes, there is software available for free that does this). If they are successful in exposing the password, they will immediately try to use the same password to access other applications on the device. Having a variety of passwords will ensure that even though a single password was exposed, it cannot be used to access other devices.
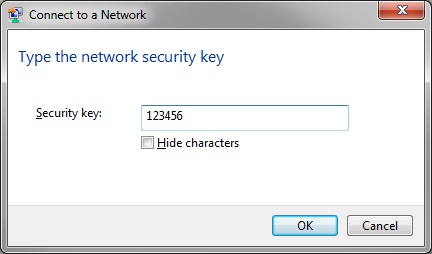
Let’s imagine that a hacker has access to your network and needs a password to access critical information. The hacker may implement what is known as a “brute force attack,” which will attempt to use every possible combination of characters to eventually discover the correct password. These attacks take time, but are very thorough. By using special characters in your password you add additional security by requiring that the brute force software also check for those special characters. The reason why length is most important is because as you increase the length of your password, you also increase the amount of possible combinations the brute force software must check. Eventually, due to length and complexity of your password, a brute-force attack becomes inefficient and would take too long to successfully discover the password.
There is simply no legitimate excuse to not creating secure and unique passwords for critical devices.
Mistake #5: Slow Internet
It’s important to have an internet connection with enough bandwidth to support the needs of your business. For example, if you collaborate with a massive amount of emails, and your business does full backups to the cloud (over the internet), you may see slowdowns in internet and email performance throughout the day because of poor internet speeds.
This is typically easy to spot. If files and emails take a considerable amount of time to download, or if you find internet service tends to lag, you may need to look into upgrading your connection. Your choice of service providers will vary in your area, and they can help you determine the right amount of bandwidth for the company with respect to workflow, amount of workstations, and other variables.
Mistake #6: Email Inefficiency
Email may be the bloodstream of your business. Email is used to carry messages, projects, ideas, and everything else the business relies on to communicate with its essential parts. It’s important to ensure that email is arriving and dispatching reliably and on time.
A small investment in an email management program can help streamline your workload by acting as a checkpoint between your email and the outside world. Companies such as and Proofpoint and Symantec offer solutions for inbound email security, outbound data loss prevention, privacy protection, email encryption, electronic discovery and email archiving. An example of how this service can be helpful is that it will hold onto inbound and outbound emails that were unsuccessfully delivered to their recipient, and will attempt to send them again once a connection is re-established. As a result, emails are not lost even if service is down, and customers and clients who send emails will not see an undelivered report or assume that the business’ email address was incorrect.
Mistake #7: Not Outsourcing IT Support
Companies can outsource their IT needs to a managed services provider who then assumes the responsibility of proactive and preventative maintenance of the IT systems within the business, and costs much less than hiring a single technician in-house. This includes onsite and remote support, emergency after-hours support, virus removal, backups, monitoring, installations, and more. Managed services providers will tailor a solution specifically for the needs of the business, and there is no harm in contacting a provider in your area to see what they may be able to do for you.
In Conclusion
In my opinion, understanding the need for proactive and preventative care for our business technology should be as simple as justifying car insurance for our vehicles, or medical insurance for our health, but apparently this is not yet the case. The truth is that technology may be the largest single investment that a small business makes. It is important to secure and maintain that investment – and take advantage of all it has to offer – to continue growing at the fastest possible pace while avoiding major costs in the future.
Business & Finance Articles on Business 2 Community
(328)