HUMAN Shuts Down Operation Accounting For 12B Fraudulent Ad Requests Daily
HUMAN Security’s Satori Threat Intelligence and Research Team uncovered and took down a sophisticated ad fraud operation dubbed VASTFLUX consisting of more than 1,700 spoofed apps targeting 120 publishers.
The ads ran in apps across nearly 11 million devices, and reached a peak volume of 12 billion ad requests daily.
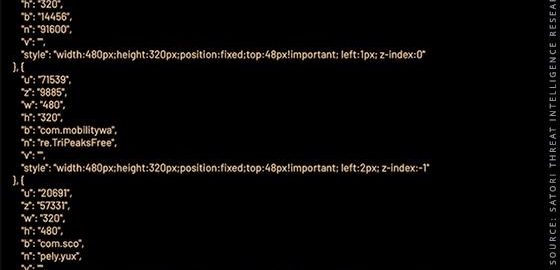
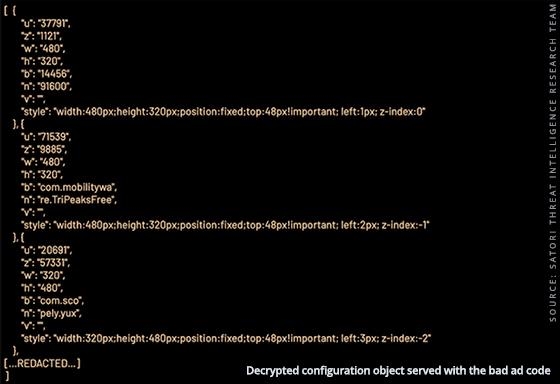
VASTFLUX injected malicious JavaScript code into digital ads running across programmatic systems, allowing the fraudsters to stack dozens of video ads on top of one another and registering views for ads completely invisible to the user.
The team identified unexpected web traffic patterns passing through a popular app, and while digging through that app, found what the company refers to as a “rabbit hole” that just got deeper.
There are substantial differences in how and where ads are delivered. Ads running in apps pass less information to verification providers than ads that run on pages visited within a web browser.
That information gap appeals to fraudsters, so they may target ads that run in more restricted environments with hope it will take longer for the scheme to be spotted and stopped.
Those behind VASTFLUX must have known this and targeted not just in-app advertising, but in-app advertising on iOS, where the environment is especially strict due to Apple’s latest privacy policies, according to the company.
The operation has been shut down, but HUMAN continues to monitor the VASTFLUX operators.
The name of the malware comes from the concept of fast flux, an evasion technique used by cybercriminals, and VAST, the Digital Video Ad Serving Template that was exploited. The company’s calling it the biggest operation uncovered by HUMAN’s team.
The Satori team found VASTFLUX while investigating an iOS app that was heavily impacted by an app spoofing attack.
VAST fraud has evolved to spoofing bids in one platform to make them appear in another platform, the company said.
The takedown comes just three months after the Satori Team announced the disruption of Scylla, a fraud operation targeting advertising software development kits (SDKs) within 9 apps on the Apple App Store and 80 Android apps on the Google Play Store, which collectively were downloaded more than 13 million times.
(13)
Report Post